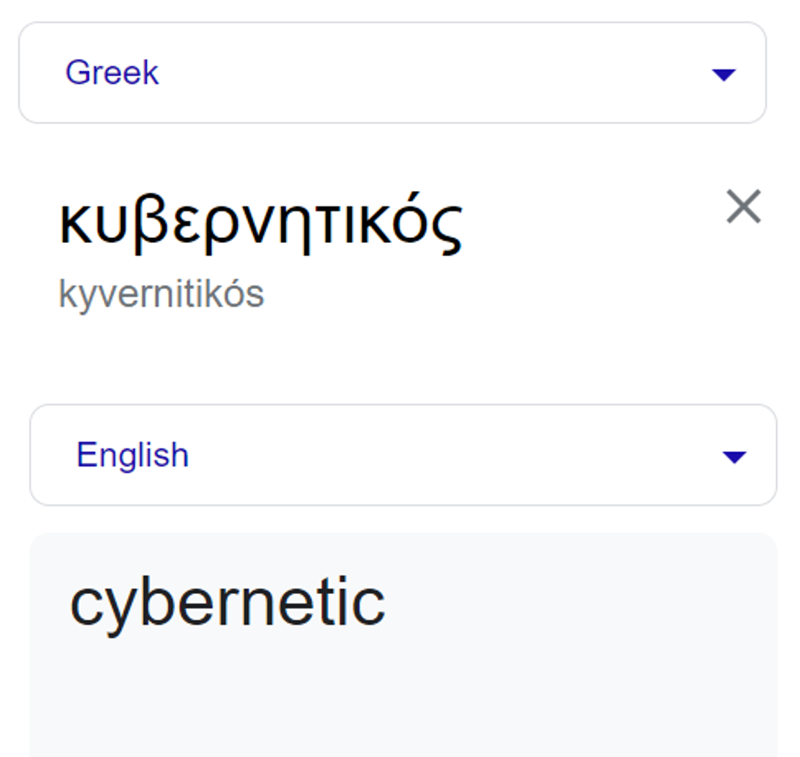
Cybernetics originally comes from the ancient Greek word kubernetikos, which means “good at steering or piloting.”
Introduction
Cyber, an abbreviation of cybernetics, is a word we use currently to talk about things that happen on computers and the internet. It also relates to cyberspace, the creation of computer networks in a world filled with human actors and artificially intelligent beings. When you use your computer, tablet, or phone to play games, watch videos, and talk to your friends online – all those things are part of the 'cyber' world.
Cyberspace, where you are right now, reading this, is an immersive world inside your digital device, on the internet, in the digital cloud environment, where you can discover and learn. Just like in the real world, you have to be safe and smart when you are in this cyber world. Just like in the real world, you need to behave in a manner that is respectful of others and is responsible for the actions that you take.
Hygiene is described as conditions or practices that help to maintain health and prevent disease, especially through cleanliness.
Cyber hygiene is the practices and steps that users of computers and other devices take to maintain the system's health at their device level and improve their online security. These practices include the safety of their identity and other personal details that could be stolen or corrupted by malicious actors.
Good cyber hygiene is necessary to keep your cyberspace safe and in good health. Paying attention to your actions online and being attentive will prevent malware, computer viruses, and other unwanted actions by other cyberspace users from affecting your well-being.
Did you know?
There are more than 1 Billion Malware Programs
- Before eating
- After handling soil
- When you see your hands dirty
- When you see others washing hands
- After going to the toilet
- Before cooking
- When coming home from school
- After eating
- After sports
- After playing with pets
- Before praying
- Before holding a baby
- After visiting a sick person
- During praying
- While singing
- Before and after reading
- Before putting on the left sock
- After opening the door

- After received new credentials
- When you notice that someone else has used your account
- After you forgot to log out from a public computer
- When you forgot your password at home
- After sharing food with your friend
- When you have lost your sweater
- When you have lost your device
- Every 6 months after changing password
- When your friend knows your password
- When you realise that your password is weak
- When the platform recommends changing
- When you have not done your homework
- On your birthday
- When you get a new device

Password
You and your family have keys to lock and unlock your doors. A password is a special digital key for your online accounts. For the security and privacy of all the items and people in your house, you can not allow someone to take your house keys and come into your home. Similarly, you don't want people to get into your online account without your permission. Your password is a secret word or code that only you should know. It performs a secret handshake with your computer or phone and through it with an online environment. When you type in your password, it tells your device, 'Sasa, it's me, and I have permission to use this.'
To make sure your password is strong and secure, it should use a mix of letters, numbers, and some symbols. This makes it really difficult for anyone else to guess.
Just like you wouldn't share your house key with anyone except your family, you should only share your password with your parents or someone you trust. They can help you keep you and your online activities safe.

A password is like a digital key to your online world, and you should keep it a secret, make it strong, and only share it with your trusted grown-ups."


- Password
- 1QAZ2wsx3EDC$edc
- qwerty
- OneBeautifu1$unnyDay
- qwerty123
- Mike123
- vUftYjBt9q
- aa1234567
- 12345
- 111111111
- M3rcedesA4
- 2X2is4&4X4is16
- M0mb@$a!
- G!r@ffe?
Methods for creating strong and memorable passwords
Creating strong passwords that are also easy to remember can be a bit challenging. Different people find different methods easier. It is important to try a variety of ways to create passwords to see which ones are the easiest for you to remember, while still being difficult for others to guess.
A strong password is a minimum ofcharacters.
A strong password has at least one , one , one and .
In a strong passworduse personal information like your name and birthdate.
predictable patterns, e.g. "12345," or "qwerty" or "asdfg" in your password.
Four methods of password creation
- Meaningful phrase
Think of a phrase or sentence that's meaningful to you. It could be a favorite quote, song lyric, or something unique to your life. For example, "I love visiting my uncle Brian". It is already more than 8 characters long and has small letters and capital letters. Now, to create a password out of it, you need to add a symbol and a number, and make it into a single "word", like this:
IL0veVisitingMyUncleBrian!
Do you see the number 0 in the word Love?

- Use substitutions
Pick a word, maybe something you like. Make sure it is at least 8 characters long. How about "chocolate"? Turn your word into a password by using substitutions. For instance,
o = 0
l = 1
a = @
Using the phrase, you might get "Ch0c01@te"
Or a word like "football" could become "F00tb@11!" with an exclamation mark to top it off.
0 = O
1 = I or L or !
2 = Z
3 = E
4 = h or A or y
5 = S
6 = b or G
7 = T
@ = a
$ = S
- Number and letter combinations
Once again, pick a word. For example "textbook". Simply place a number after each letter and then choose a symbol to end it with. Something like this "T1e2x3t4b5o6o7k?".
Or you could pick a mathematical equation 1+1=2 and make a password "1plus1is2!".
- Keyboard patterns
This time around you will think of the keyboard in front of you as consisting of little cubes, not of letters, symbols, and numbers. These cubes could form different patterns.
Have a look at the blue circle. It forms the password "5Rfvbnju&6" when typed by pressing the shift button on two occasions along its path.
There is also the purple zigzag that forms a password "Xft6ujmko)".
The pink squares have "!2WQ89oiTYHG" as the password.
When using keyboard patterns, be aware that some shapes will look different on some keyboards. Do practice your hand movement, but be aware of the final password composition.

Keep In Mind
- Be sure to practice your password.
- You can keep it also written down on paper, keeping the paper in a safe location, like at the bottom of a drawer, or between other papers. On the paper, do not include the name of the portal that the password is for.
- You can ask your parent(s) to keep a copy of your password safely for you.
- Be sure not to save your password in the browser memory when using a public computer access point - a cyber cafe, school computer lab, or a friend's device. This would be a major threat to the safety of your digital identity.
I Have Forgotten My Password
If you have forgotten your password, you can recover or reset it. Most websites have methods for password reset. This is done through:
- a secondary mail address
- a two-factor authentication
- system administrator
- one-time password (OTP)
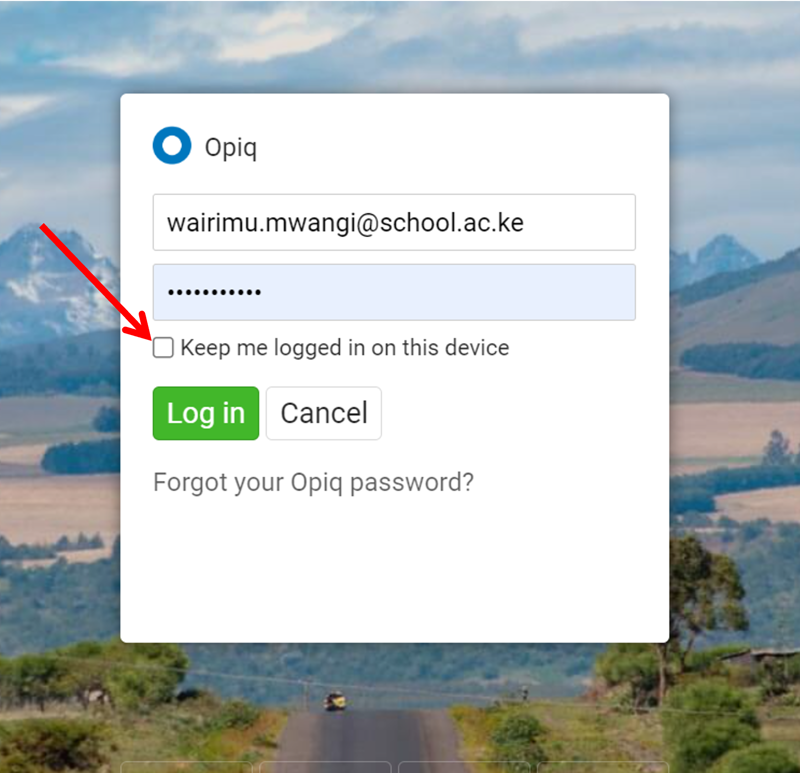
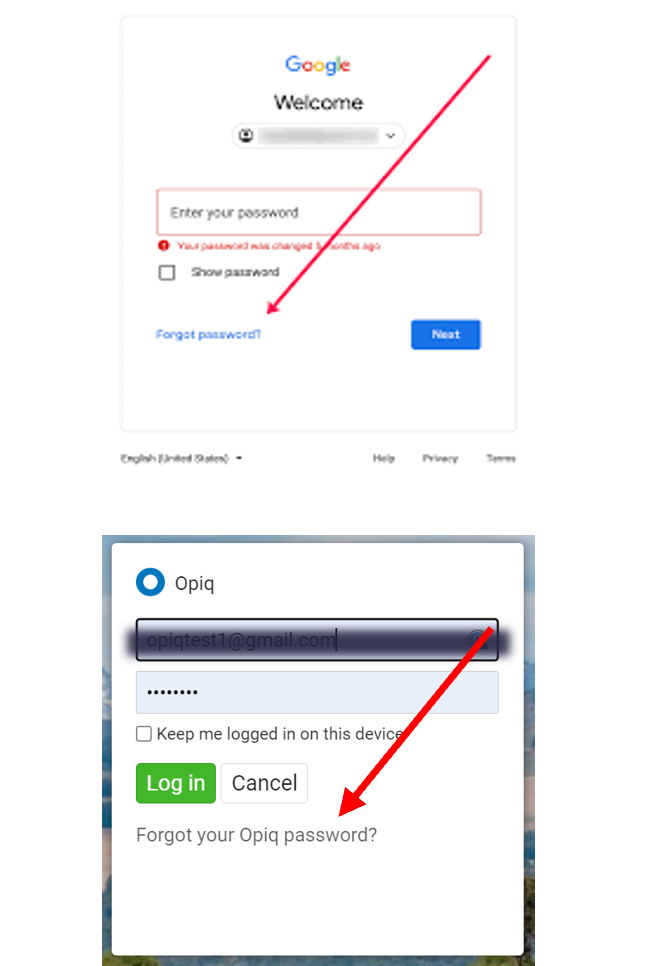
When you have forgotten your Opiq password, click on the "Forgot your Opiq password?". Then, if your account is set up with your email address, you will enter your Opiq user ID (e-mail) and you will receive a link in your email to reset your password. If your user ID is not an email address, you will contact your school administrator to recover your password or to set a new password for you.
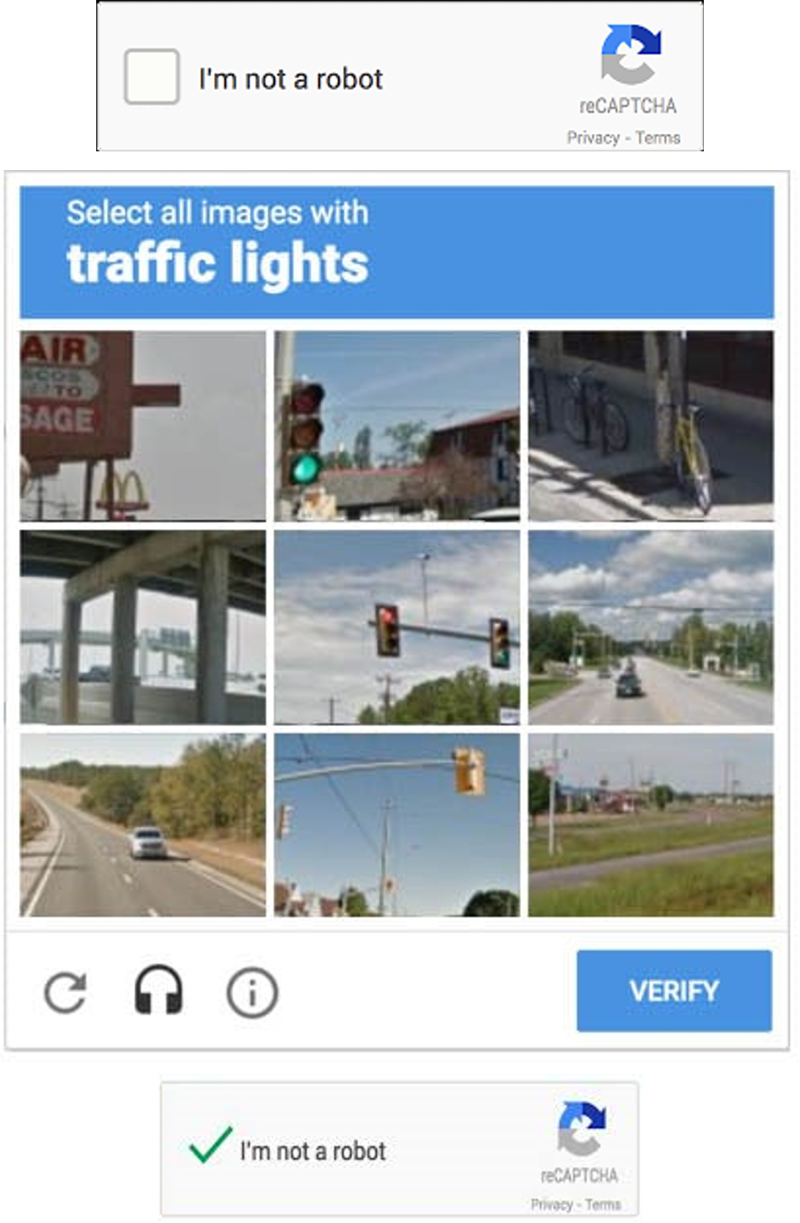
Are you a robot?
The cyberspace that we have described here, just like the real world, clearly has both good people and bad people. Beyond that, it also has good artificial intelligence and bad artificial intelligence. Bad, or malicious artificial intelligence is designed to interfere with the operations of systems, websites, web portals. These cyber attacks, launched by cyber criminals with the use of malware programs, cause huge losses to businesses and are a threat to digital systems across all sectors.
Websites and web portals use digital tools to verify that the interaction is taking place with a human being and not a robot, also called bot or cyber bot. One of the tools is described as the completely automated public Turing test to tell computers and humans apart, abbreviated as CAPTCHA.
- Completely Automated: It means the test is done by a computer automatically, without any human help.
- Public: It's a test that anyone on the internet can take.
- Turing test: This part is named after a famous computer scientist, Alan Turing. He came up with the idea that if a computer can have a conversation with a human and the human can't tell it's a computer, then the computer is really smart.
That is what CAPTCHA is meant to do, have a conversation in the form of simple tasks like identifying pictures or typing letters and numbers. When you see a CAPTCHA, it's like a game that you have to play for a few seconds to prove you're a real person, not a computer program. It helps protect websites from things like spam, fake accounts, and hackers because it can be tricky for computers to solve some of these puzzles that you, as a human find quite easy.
When you ignore the CAPTCHA question, OR fail to click on the correct squares, OR answer incorrectly several times, the portal will assume that you are indeed a robot!